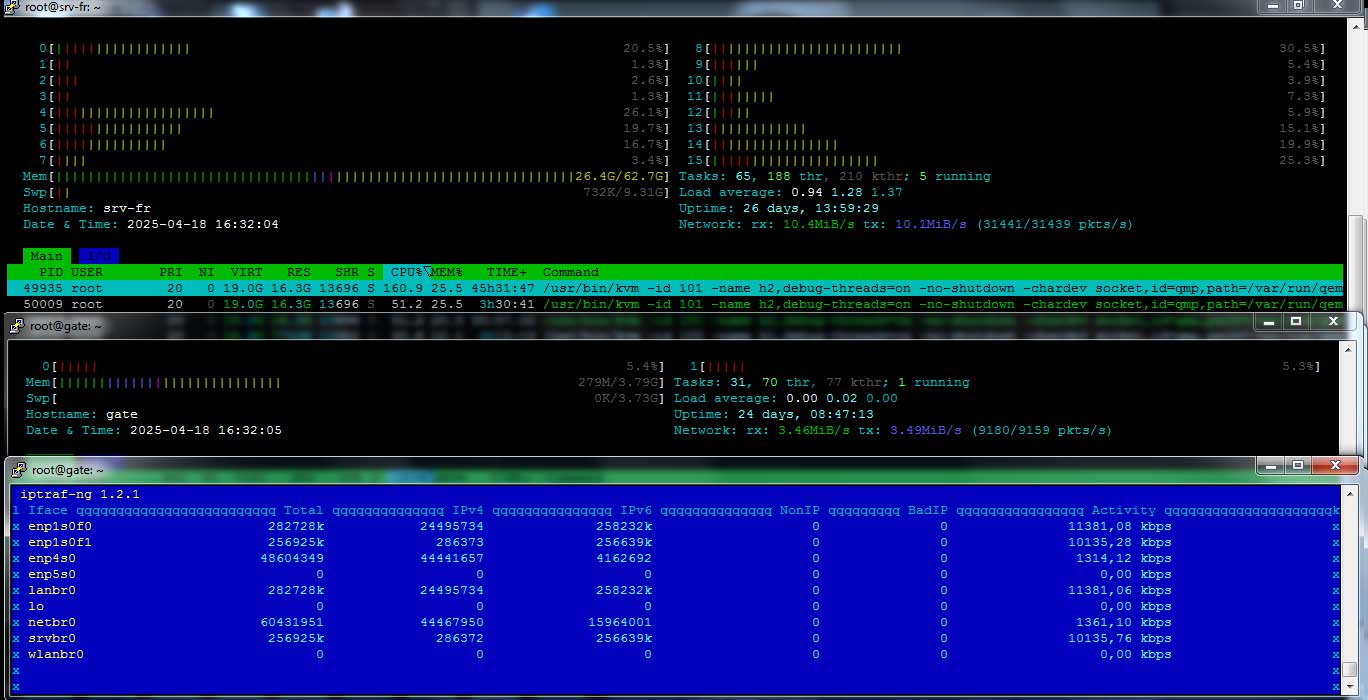
La configuration réseau Fibre - IP❤6 - ULA (Unique Local Address) de chez moi jusqu’aux serveurs ; en image : Sympat, non… 
Je « me » fais un récapitulatif de l’installation Post-quantum strongSwan v6 (vérifier si liboqs 0.9.2 et strongswan-6.0.0beta6 n’ont pas évolués) :
Installation
# Installation de la version non officielle StrongSwan qui utilise la librairie OQS (OpenQuantumSafe) des algorhitmes cryptographiques.
apt-get -y install iproute2 iputils-ping nano wget unzip bzip2 make gcc libssl-dev cmake ninja-build
mkdir /liboqs && \
cd /liboqs && \
wget https://github.com/open-quantum-safe/liboqs/archive/refs/tags/0.9.2.zip && \
unzip 0.9.2.zip && \
cd liboqs-0.9.2 && \
mkdir build && cd build
cmake -GNinja -DOQS_USE_OPENSSL=ON -DBUILD_SHARED_LIBS=ON -DCMAKE_INSTALL_PREFIX=/usr \
-DCMAKE_BUILD_TYPE=Release -DOQS_BUILD_ONLY_LIB=ON .. && ninja && ninja install
cd / && rm -R /liboqs
mkdir /strongswan-build && \
cd /strongswan-build && \
wget https://download.strongswan.org/strongswan-6.0.0beta6.tar.bz2 && \
tar xfj strongswan-6.0.0beta6.tar.bz2 && \
cd strongswan-6.0.0beta6
./configure --prefix=/usr --sysconfdir=/etc --with-systemdsystemunitdir=/lib/systemd/system --disable-ikev1 --disable-constraints --enable-openssl --enable-frodo --enable-oqs --enable-silent-rules --enable-eap-identity --enable-eap-md5 --enable-eap-mschapv2 --enable-eap-tls --enable-eap-ttls --enable-eap-peap --enable-eap-tnc --enable-eap-dynamic --enable-eap-radius --enable-xauth-eap --enable-dhcp --enable-addrblock --enable-unity --enable-certexpire --enable-radattr
make all && make install
# --
# Au cas où, vous avez une version strongSwan 5.XX qui cause de conflits avec la version compilée.
# dpkg -r strongswan-swanctl charon-systemd libcharon-extra-plugins strongswan-libcharon
# ./configure [...] --with-systemdsystemunitdir=/lib/systemd/system
# systemctl unmask strongXswan.service
# systemctl enable strongXswan.service
# systemctl restart strongXswan.service
# systemctl status strongXswan.service
Connexions (swanctl --load-conns)
Les connexions établies StrongSwan :
root@lab3w:/etc/swanctl # swanctl --list-sas
ca-fr: #8, ESTABLISHED, IKEv2, ad2daa13344fbeae_i 130c69bc0eb38f5b_r*
local 'srv.ca.lab3w.com' @ 158.69.126.137[4500]
remote 'srv.fr.lab3w.com' @ 109.210.56.240[4500] [fec1::1]
AES_CBC-256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3/KE4_HQC_L5
established 1698s ago, rekeying in 12654s
ca-fr: #58, reqid 1, INSTALLED, TUNNEL-in-UDP, ESP:AES_CBC-256/HMAC_SHA2_256_128/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3/KE4_HQC_L5
installed 24s ago, rekeying in 138s, expires in 174s
in ca06e0ea, 0 bytes, 0 packets
out c363d438, 0 bytes, 0 packets
local fc00:41d0:701:1100::/64 fc00:41d0:801:2000::/64 fc00:5300:60:9389::/64 fec0::/16 fec2::1/128 fec3::1/128
remote fc01::10:106:0:0/104 fc01::10:126:42:0/112 fc01::172:16:0:0/104 fc01::192:168:0:0/104 fec1::/16
ca-uk: #12, ESTABLISHED, IKEv2, fbf8d917a028b5fa_i 27993e66b43d5756_r*
local 'srv.ca.lab3w.com' @ 158.69.126.137[4500]
remote 'vps.uk.ipv10.net' @ 57.128.171.43[4500] [fec2::1]
AES_CBC-256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3/KE4_HQC_L5
established 1000s ago, rekeying in 12747s
ca-uk: #59, reqid 4, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3
installed 3s ago, rekeying in 171s, expires in 195s
in c859d552, 0 bytes, 0 packets
out cdfbc2ee, 0 bytes, 0 packets
local fc00:41d0:701:1100::/64 fc00:5300:60:9389::/64 fc01::10:106:0:0/104 fc01::10:126:42:0/112 fc01::172:16:0:0/104 fc01::192:168:0:0/104 fec0::/16 fec1::/16
remote fc00:41d0:801:2000::/64 fec2::1/128
ca-de: #2, ESTABLISHED, IKEv2, ddc7ac4975d4e081_i 97ce2741655d20ea_r*
local 'srv.ca.lab3w.com' @ 158.69.126.137[4500]
remote 'vps.de.ipv10.net' @ 135.125.133.51[4500] [fec3::1]
AES_CBC-256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3/KE4_HQC_L5
established 2715s ago, rekeying in 10567s
ca-de: #57, reqid 3, INSTALLED, TUNNEL, ESP:AES_CBC-256/HMAC_SHA2_256_128/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3
installed 69s ago, rekeying in 110s, expires in 129s
in c670c894, 0 bytes, 0 packets
out c6945952, 0 bytes, 0 packets
local fc00:41d0:801:2000::/64 fc00:5300:60:9389::/64 fc01::10:106:0:0/104 fc01::10:126:42:0/112 fc01::172:16:0:0/104 fc01::192:168:0:0/104 fec0::/16 fec1::/16 fec2::1/128
remote fc00:41d0:701:1100::/64 fec3::1/128
Credits (swanctl --load-creds)
Les autorités :
root@lab3w:/etc/swanctl # swanctl --list-authorities
strongswan:
cacert: C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072
Les certificats :
root@lab3w:/etc/swanctl # swanctl --list-certs
List of X.509 End Entity Certificates
subject: "C=FR, O=LAB3W, CN=srv.ca.lab3w.com"
issuer: "C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072"
validity: not before Oct 30 07:24:39 2024, ok
not after Oct 30 07:24:39 2029, ok (expires in 1824 days)
serial: 01
altNames: srv.ca.lab3w.com
flags:
authkeyId: 95:66:e0:e9:97:2d:7b:cb:ee:3d:7b:e3:95:5f:10:19:bc:6e:71:d5
subjkeyId: 4e:f4:60:60:83:f5:53:a7:53:7d:4d:b8:9b:74:4b:d4:6c:35:d4:f6
pubkey: Falcon1024 14344 bits, has private key
keyid: 28:78:34:78:37:e1:92:9f:91:e5:76:58:5f:e3:40:d8:23:03:aa:c9
subjkey: 4e:f4:60:60:83:f5:53:a7:53:7d:4d:b8:9b:74:4b:d4:6c:35:d4:f6
subject: "C=FR, O=LAB3W, CN=srv.fr.lab3w.com"
issuer: "C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072"
validity: not before Oct 30 06:48:28 2024, ok
not after Oct 30 06:48:28 2029, ok (expires in 1824 days)
serial: 01
altNames: srv.fr.lab3w.com
flags:
authkeyId: 95:66:e0:e9:97:2d:7b:cb:ee:3d:7b:e3:95:5f:10:19:bc:6e:71:d5
subjkeyId: 19:b5:62:8f:31:fc:27:a6:01:45:bc:d3:75:d4:be:07:7f:59:b8:aa
pubkey: Falcon1024 14344 bits, has private key
keyid: ce:3b:8e:ea:f0:bb:c9:2b:8b:18:7b:9c:f5:e9:24:6a:cf:fd:82:72
subjkey: 19:b5:62:8f:31:fc:27:a6:01:45:bc:d3:75:d4:be:07:7f:59:b8:aa
subject: "C=FR, O=LAB3W, CN=vps.uk.ipv10.net"
issuer: "C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072"
validity: not before Nov 01 02:51:21 2024, ok
not after Nov 01 02:51:21 2029, ok (expires in 1825 days)
serial: 01
altNames: vps.uk.ipv10.net
flags:
authkeyId: 95:66:e0:e9:97:2d:7b:cb:ee:3d:7b:e3:95:5f:10:19:bc:6e:71:d5
subjkeyId: 02:26:c7:d4:59:22:c5:51:64:6a:6e:95:6f:f0:ae:21:ea:8d:f9:1c
pubkey: Falcon1024 14344 bits, has private key
keyid: 96:89:2f:cd:02:5c:80:1e:a6:dc:3e:42:f5:b0:76:15:62:30:c6:4a
subjkey: 02:26:c7:d4:59:22:c5:51:64:6a:6e:95:6f:f0:ae:21:ea:8d:f9:1c
subject: "C=FR, O=LAB3W, CN=vps.de.ipv10.net"
issuer: "C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072"
validity: not before Nov 01 03:29:17 2024, ok
not after Nov 01 03:29:17 2029, ok (expires in 1825 days)
serial: 01
altNames: vps.de.ipv10.net
flags:
authkeyId: 95:66:e0:e9:97:2d:7b:cb:ee:3d:7b:e3:95:5f:10:19:bc:6e:71:d5
subjkeyId: f3:07:2f:87:81:67:7d:66:b2:e7:7a:00:3f:87:70:69:c7:63:28:28
pubkey: Falcon1024 14344 bits, has private key
keyid: 08:34:b3:1c:ca:71:b2:a4:24:69:e7:86:1c:b9:14:b1:bd:9d:63:7d
subjkey: f3:07:2f:87:81:67:7d:66:b2:e7:7a:00:3f:87:70:69:c7:63:28:28
List of X.509 CA Certificates
subject: "C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072"
issuer: "C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072"
validity: not before Oct 30 06:37:36 2024, ok
not after Oct 30 06:37:36 2034, ok (expires in 3650 days)
serial: 11:f6:b6:9e:4f:22:12:bc
flags: CA CRLSign self-signed
subjkeyId: 95:66:e0:e9:97:2d:7b:cb:ee:3d:7b:e3:95:5f:10:19:bc:6e:71:d5
pubkey: RSA 3072 bits, has private key
keyid: cf:4b:7c:c6:cc:38:ac:5b:77:5f:f2:e7:32:31:8c:0c:64:ab:0a:58
subjkey: 95:66:e0:e9:97:2d:7b:cb:ee:3d:7b:e3:95:5f:10:19:bc:6e:71:d5
Files
Les fichiers sur le serveur :
root@lab3w:/etc/swanctl # tree
.
├── conf.d
│ ├── ca-de.conf
│ ├── ca-fr.conf
│ └── ca-uk.conf
├── ecdsa
├── pkcs12
├── pkcs8
├── private
│ ├── LAB3W_ZW3B-caKey-rsa_3072.pem
│ ├── srv.ca.lab3w.com-Key-falcon1024.pem
│ ├── srv.fr.lab3w.com-Key-falcon1024.pem
│ ├── vps.de.ipv10.net-Key-falcon1024.pem
│ └── vps.uk.ipv10.net-Key-falcon1024.pem
├── pubkey
├── rsa
├── swanctl.conf
├── tmp
│ ├── srv.ca.lab3w.com-Req.pem
│ ├── srv.fr.lab3w.com-Req.pem
│ ├── vps.de.ipv10.net-Req.pem
│ └── vps.uk.ipv10.net-Req.pem
├── x509
│ ├── srv.ca.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
│ ├── srv.fr.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
│ ├── vps.de.ipv10.net-Cert-falcon1024-sign_ca-rsa_3072.pem
│ └── vps.uk.ipv10.net-Cert-falcon1024-sign_ca-rsa_3072.pem
├── x509aa
├── x509ac
├── x509ca
│ └── LAB3W_ZW3B-caCert-rsa_3072.pem
├── x509crl
└── x509ocsp
14 directories, 18 files
Les fichiers sur un client :
root@pve:/etc/swanctl # tree
.
├── conf.d
│ └── fr-ca.conf
├── ecdsa
├── pkcs12
├── pkcs8
├── private
│ └── srv.fr.lab3w.com-Key-falcon1024.pem
├── pubkey
├── rsa
├── swanctl.conf
├── x509
│ └── srv.fr.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
├── x509aa
├── x509ac
├── x509ca
│ └── LAB3W_ZW3B-caCert-rsa_3072.pem
├── x509crl
└── x509ocsp
14 directories, 5 files
Conf
La configuration sur le serveur :
Infos : File « /etc/strongswan.conf » par default.
root@lab3w:/etc/swanctl # vim /etc/strongswan.conf
charon {
load_modular = yes
plugins {
include strongswan.d/charon/*.conf
}
start-scripts {
creds = swanctl --load-creds
conns = swanctl --load-conns
pools = swanctl --load-pools
}
filelog {
charon {
path = /var/log/charon.log
# add a timestamp prefix
time_format = %b %e %T
# prepend connection name, simplifies grepping
ike_name = yes
# overwrite existing files
append = no
# increase default loglevel for all daemon subsystems
default = 1
tls = 2
ike = 2
# flush each line to disk
flush_line = yes
}
# and two loggers using syslog
syslog {
# prefix for each log message
identifier = charon-custom
# use default settings to log to the LOG_DAEMON facility
daemon {
}
# very minimalistic IKE auditing logs to LOG_AUTHPRIV
auth {
default = -1
ike = 0
}
}
}
eap-dynamic {
prefer_user = yes
preferred = md5, tls
}
send_vendor_id = yes
prefer_configured_proposals = no
fragment_size = 1480
max_packet = 30000
# install_routes = no
# install_virtual_ip = yes
# install_virtual_ip_on = vti1
# interfaces_use = vti0
# interfaces_ignore = vmbr0
}
include strongswan.d/*.conf
pki {
# load = plugins: random drbg x509 pubkey pkcs1 pkcs8 pkcs12 pem openssl oqs
}
# for strongSwan 5.9
libtls {
version_max = 1.3
suites = TLS_AES_128_GCM_SHA256,TLS_AES_256_GCM_SHA384
}
root@lab3w:/etc/swanctl # vim swanctl.conf
connections {
include conf.d/ca-fr.conf
include conf.d/ca-uk.conf
include conf.d/ca-de.conf
}
authorities {
strongswan {
cacert = LAB3W_ZW3B-caCert-rsa_3072.pem
# crl_uris = http://ip6-winnetou.strongswan.org/strongswan.crl
}
}
pools {
rw_pool {
addrs = 172.16.1.100-172.16.1.200
}
fr-ipv6 {
addrs = fec1::1/16
}
uk-ipv6 {
addrs = fec2::1/128
}
de-ipv6 {
addrs = fec3::1/128
}
}
secrets {
# PSK
ike-my_pseudo {
id = my_pseudo
secret = 0sTdD7IOindSa6FuyjLsWtsdD9o/1a
}
# EAP
eap-my_pseudo {
id = my_pseudo@doman.tld
secret = my_password
}
}
root@lab3w:/etc/swanctl # vim conf.d/ca-fr.conf
ca-fr {
remote_addrs = 109.210.56.240
pools = fr-ipv6
local {
auth = pubkey
certs = srv.ca.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
id = srv.ca.lab3w.com
}
remote {
auth = pubkey
id = srv.fr.lab3w.com
}
children {
ca-fr {
# mode = transport
local_ts = fec0::1/16, fc00:5300:60:9389::/64, fec2::1/128, fc00:41d0:801:2000::/64, fec3::1/128, fc00:41d0:701:1100::/64
remote_ts = fec1::1/16, fc01::10:106:42:0/104, fc01::10:126:42:0/112, fc01::172:16:0:0/104, fc01::192:168:8:0/104
start_action = trap
#-----
# ESP
# DEFAUT : no cipher
# selected proposal: ESP:AES_GCM_16_128/NO_EXT_SEQ
# ok
esp_proposals = aes256-sha256-x25519-ke1_kyber3-ke2_bike3-ke3_hqc3-ke3_none-ke4_hqc5-ke4_none
#-----
# rekey_time = 5400 # 90min default
rekey_time = 180 # 3min
rekey_bytes = 500000000
rekey_packets = 1000000
}
}
#-----
# IKE
version = 2
dpd_delay = 60s
# DEFAULT : no cipher config
# selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256
# ok
proposals = aes256-sha256-x25519-ke1_kyber3-ke1_frodoa3-ke2_bike3-ke2_hqc3-ke3_hqc3-ke3_none-ke4_hqc5-ke4_none
# selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3/KE4_HQC_L5
#-----
}
La configuration sur un client (le fichier /etc/strongswan.conf ne change pas) :
root@pve:/etc/swanctl # vim swanctl.conf
connections {
include conf.d/fr-ca.conf
}
authorities {
strongswan {
cacert = LAB3W_ZW3B-caCert-rsa_3072.pem
# crl_uris = http://ip6-winnetou.strongswan.org/strongswan.crl
}
}
pools {
}
secrets {
}
# Include config snippets
include conf.d/*.conf
root@pve:/etc/swanctl # vim conf.d/fr-ca.conf
fr-ca {
remote_addrs = 158.69.126.137
local {
auth = pubkey
certs = srv.fr.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
id = srv.fr.lab3w.com
}
remote {
auth = pubkey
id = srv.ca.lab3w.com
}
children {
fr-ca {
# mode = transport
local_ts = fec1::1/16, fc01::172:16:0:0/104, fc01::10:106:42:0/104, fc01::10:126:42:0/112, fc01::192:168:8:0/104
remote_ts = fec0::1/16, fc00:5300:60:9389::/64, fec2::1/128, fc00:41d0:801:2000::/64, fec3::1/128, fc00:41d0:701:1100::/64
#-----
start_action = trap
#-----
# ESP
# DEFAUT : no cipher
# selected proposal: ESP:AES_GCM_16_128/NO_EXT_SEQ
# ok
esp_proposals = aes256-sha256-x25519-ke1_kyber3-ke2_bike3-ke3_hqc3-ke3_none-ke4_hqc5-ke4_none
# selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ
#-----
# rekey_time = 5400 # 90min default
# rekey_bytes = 500000000
# rekey_packets = 1000000
}
}
#-----
# IKE
version = 2
dpd_delay = 60s
# DEFAULT : no cipher config
# selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256
# ok
proposals = aes256-sha256-x25519-ke1_kyber3-ke1_frodoa3-ke2_bike3-ke2_hqc3-ke3_hqc3-ke3_none-ke4_hqc5-ke4_none
# selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/CURVE_25519/KE1_KYBER_L3/KE2_BIKE_L3/KE3_HQC_L3/KE4_HQC_L5
#-----
}
Voilà la configuration est prête.
Ci-dessous la création des certificats SSL :
# Creation de clefs de l'autorité de certificats
pki --gen --type rsa --size 3072 --outform pem > /etc/swanctl/private/LAB3W_ZW3B-caKey-rsa_3072.pem
# Création des certificats de l'autorité (certificat auto-signé)
pki --self --ca --type rsa --in /etc/swanctl/private/LAB3W_ZW3B-caKey-rsa_3072.pem --lifetime 3652 --dn "C=FR, O=LAB3W, CN=ZW3B Cyber Root CA : rsa_3072" --outform pem > /etc/swanctl/x509ca/LAB3W_ZW3B-caCert-rsa_3072.pem
En passant pour installer votre autorité sur votre machine Windows il faut ce type de fichier (par exemple « LAB3W_ZW3B-caCert-rsa_3072.der ») ;
# Fichier de l'autorité au format Windows (pour pouvoir l'importer)
openssl x509 -in /etc/swanctl/x509ca/LAB3W_ZW3B-caCert-rsa_3072.pem -out /etc/swanctl/x509ca/LAB3W_ZW3B-caCert-rsa_3072.der -outform DER
Serveur CA (srv.ca.lab3w.com) debian 10 (buster) pq-strongswan 6.0
# falcon1024
pki --gen --type falcon1024 --outform pem > /etc/swanctl/private/srv.ca.lab3w.com-Key-falcon1024.pem
pki --req --type priv --in /etc/swanctl/private/srv.ca.lab3w.com-Key-falcon1024.pem \
--dn "C=FR, O=LAB3W, CN=srv.ca.lab3w.com" \
--san srv.ca.lab3w.com --outform pem > /etc/swanctl/tmp/srv.ca.lab3w.com-Req.pem
# Signature rsa_3072
pki --issue --cacert /etc/swanctl/x509ca/LAB3W_ZW3B-caCert-rsa_3072.pem --cakey /etc/swanctl/private/LAB3W_ZW3B-caKey-rsa_3072.pem \
--type pkcs10 --in /etc/swanctl/tmp/srv.ca.lab3w.com-Req.pem --serial 01 --lifetime 1826 \
--outform pem > /etc/swanctl/x509/srv.ca.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
Serveur FR (srv.fr.lab3w.com) debian 12 (bookworm) pq-strongswan 6.0
# falcon1024
pki --gen --type falcon1024 --outform pem > /etc/swanctl/private/srv.fr.lab3w.com-Key-falcon1024.pem
pki --req --type priv --in /etc/swanctl/private/srv.fr.lab3w.com-Key-falcon1024.pem \
--dn "C=FR, O=LAB3W, CN=srv.fr.lab3w.com" \
--san srv.fr.lab3w.com --outform pem > /etc/swanctl/tmp/srv.fr.lab3w.com-Req.pem
# Signature rsa_3072
pki --issue --cacert /etc/swanctl/x509ca/LAB3W_ZW3B-caCert-rsa_3072.pem --cakey /etc/swanctl/private/LAB3W_ZW3B-caKey-rsa_3072.pem \
--type pkcs10 --in /etc/swanctl/tmp/srv.fr.lab3w.com-Req.pem --serial 01 --lifetime 1826 \
--outform pem > /etc/swanctl/x509/srv.fr.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
Et voilà, on peut lancer notre connexion :
root@lab3w:/etc/swanctl # swanctl --initiate --child ca-frPour terminer une connexion :
root@lab3w:/etc/swanctl # swanctl --terminate --ike ca-frAvec çà, on a une connexion fonctionnelle « basique » de serveur à serveur VPN utilisant StrongSwan v6 (docs).
StrongSwan permet d’autres types d’authentifications comme l’Extensible Authentication Protocol (EAP) que je n’ai pas testé, pour les réseaux mobiles, Wi-Fi et filaires pour ajouter une méthode d’authentification suplémentaire comme MD5, OTP (One-Time Passwords), Generic Token Card, SIM, etc.) comme par exemple pour les systèmes Microsoft et Cisco.
@+
Romain.
Voir un certificat avec la commande PKI :
pki --print --type x509 --in /etc/swanctl/x509/srv.fr.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem
Voir un certificat avec la commande OpenSSL :
openssl x509 -in /etc/swanctl/x509/srv.fr.lab3w.com-Cert-falcon1024-sign_ca-rsa_3072.pem -noout -text -inform pem
Les traceroutes :
C:\Users\ORJ>tracert fc00:41d0:801:2000::1
Détermination de l’itinéraire vers fc00:41d0:801:2000::1 avec un maximum de 30 sauts.
1 <1 ms <1 ms <1 ms fc01::172:16:0:254
2 97 ms 97 ms 97 ms fec0::1
3 175 ms 175 ms 175 ms fec2::1
4 174 ms 175 ms 174 ms fc00:41d0:801:2000::1
Itinéraire déterminé.
C:\Users\ORJ>tracert fc00:41d0:701:1100::1
Détermination de l’itinéraire vers fc00:41d0:701:1100::1 avec un maximum de 30 sauts.
1 <1 ms <1 ms <1 ms fc01::172:16:0:254
2 97 ms 97 ms 96 ms fec0::1
3 190 ms 190 ms 190 ms fec3::1
4 189 ms 189 ms 189 ms fc00:41d0:701:1100::1
Itinéraire déterminé.
C:\Users\ORJ>tracert fc00:5300:60:9389:15:1:a:10
Détermination de l’itinéraire vers fc00:5300:60:9389:15:1:a:10 avec un maximum de 30 sauts.
1 <1 ms <1 ms <1 ms fc01::172:16:0:254
2 97 ms 96 ms 96 ms fec0::1
3 97 ms 96 ms 97 ms fc00:5300:60:9389:15:1:0:1
4 97 ms * 96 ms fc00:5300:60:9389:15:1:a:10
Itinéraire déterminé.
C:\Users\ORJ>tracert fc00:5300:60:9389:15:2:a:10
Détermination de l’itinéraire vers fc00:5300:60:9389:15:2:a:10 avec un maximum de 30 sauts.
1 <1 ms <1 ms <1 ms fc01::172:16:0:254
2 97 ms 96 ms 97 ms fec0::1
3 96 ms 97 ms 97 ms fc00:5300:60:9389:15:2:0:1
4 96 ms 96 ms 97 ms fc00:5300:60:9389:15:2:a:10
Itinéraire déterminé.
root@lb2.ww2:~ # traceroute fc01::10:106:42:10 -I
traceroute to fc01::10:106:42:10 (fc01::10:106:42:10), 30 hops max, 80 byte packets
1 fc00:5300:60:9389:15:2:a:ffff (fc00:5300:60:9389:15:2:a:ffff) 0.052 ms 0.016 ms 0.013 ms
2 fc00:5300:60:9389:15:2:0:f (fc00:5300:60:9389:15:2:0:f) 0.165 ms 0.143 ms 0.128 ms
3 fec1::1 (fec1::1) 97.483 ms 97.476 ms 97.536 ms
4 * * *
5 fc01::10:106:42:10 (fc01::10:106:42:10) 97.534 ms * *
root@lb2.ww2:~ # traceroute fc00:41d0:801:2000::1
traceroute to fc00:41d0:801:2000::1 (fc00:41d0:801:2000::1), 30 hops max, 80 byte packets
1 fc00:5300:60:9389:15:2:a:ffff (fc00:5300:60:9389:15:2:a:ffff) 0.616 ms 0.539 ms 0.500 ms
2 fc00:5300:60:9389:15:2:0:f (fc00:5300:60:9389:15:2:0:f) 0.466 ms 0.428 ms 0.397 ms
3 fec2::1 (fec2::1) 78.224 ms 78.205 ms 78.166 ms
4 fc00:41d0:801:2000::1 (fc00:41d0:801:2000::1) 78.156 ms 78.172 ms 78.160 ms
root@lb2.ww2:~ # traceroute fc00:41d0:701:1100::1
traceroute to fc00:41d0:701:1100::1 (fc00:41d0:701:1100::1), 30 hops max, 80 byte packets
1 fc00:5300:60:9389:15:2:a:ffff (fc00:5300:60:9389:15:2:a:ffff) 0.052 ms 0.017 ms 0.016 ms
2 fc00:5300:60:9389:15:2:0:f (fc00:5300:60:9389:15:2:0:f) 0.117 ms 0.081 ms 0.070 ms
3 fec3::1 (fec3::1) 92.857 ms 92.880 ms 92.931 ms
4 fc00:41d0:701:1100::1 (fc00:41d0:701:1100::1) 92.946 ms 92.985 ms 92.959 ms
Netfilter
Je vous ajoute ces fonctions ip6tables.
IPv6 ULA : Unique Local Address (IPv4 : 10.0.0.0/8, 192.168.0.0/16, 172.16-32.0.0/12)
IPv6 GUA : Global Unique Address (IPv4 publique Internet)
Je vous ajoute ces fonctions que j’ai créais pour mon pare-feu Linux - correspondante aux addresses « ULA » et autres.
/!\ ttention, on laisse passer les requêtes locales, on adapte après, c’est pour la compréhension de ce type d’adresse.
Exemple :
#####
# we set the rules for local IPv6 addresses
#####
function ipv6_ula()
{
echo " |";
echo " + IPv6 - Addrs Unique Locale Area -----------------------";
# Allow Link-Local addresses
# network range : fc00:0000:0000:0000:0000:0000:0000:0000-fdff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
echo " |\\\\";
$IP6TABLE -A INPUT -s fc00::/7 -j ACCEPT
$IP6TABLE -A FORWARD -s fc00::/7 -d fc00::/7 -j ACCEPT
$IP6TABLE -A OUTPUT -d fc00::/7 -j ACCEPT
echo " | +--> "fc00::/7 : ACCEPT;
echo " | |";
echo " |" + IPv6 - Addrs Unique Locale Area : [OK]
}
function ipv6_multicast()
{
echo " |";
echo " + IPv6 - Addrs Multicast -----------------------";
# Allow multicast
# network range : ff00:0000:0000:0000:0000:0000:0000:0000-ffff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
echo " |\\\\";
$IP6TABLE -A INPUT -d ff00::/8 -j ACCEPT
$IP6TABLE -A FORWARD -s ff00::/8 -d ff00::/8 -j ACCEPT
$IP6TABLE -A OUTPUT -d ff00::/8 -j ACCEPT
echo " | +--> "ff00::/8 : ACCEPT;
echo " | |";
echo " |" + IPv6 - Addrs Multicast : [OK]
}
function ipv6_link_local()
{
echo " |";
echo " + IPv6 - Addrs Link-Local Unicast -----------------------";
# Allow Link-Local addresses
# network range : fe80:0000:0000:0000:0000:0000:0000:0000-febf:ffff:ffff:ffff:ffff:ffff:ffff:ffff
echo " |\\\\";
$IP6TABLE -A INPUT -s fe80::/10 -j ACCEPT
$IP6TABLE -A FORWARD -s fe80::/10 -d fe80::/10 -j ACCEPT
$IP6TABLE -A OUTPUT -d fe80::/10 -j ACCEPT
echo " | +--> "fe80::/10 : ACCEPT;
echo " | |";
echo " | "+ IPv6 - Addrs Link-Local : [OK]
}
#####
# we set the rules for secure local IPv6 addresses (VPN/strongSwan)
#####
function ipv6_strongswan()
{
# Default ------------------
echo " |";
echo " + IPv6 - Addrs Site-Local Secure Area Network -------------------------";
# Allow Secure Area Network addresses
# network range : fec0:0000:0000:0000:0000:0000:0000:0000-feff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
echo " |\\\\";
$IP6TABLE -A INPUT -s fec0::/10 -j ACCEPT
$IP6TABLE -A FORWARD -s fec0::/10 -d fec0::/10 -j ACCEPT
$IP6TABLE -A OUTPUT -d fec0::/10 -j ACCEPT
echo " | +--> "fec0::/10 : ACCEPT;
echo " | |";
echo " | "+ IPv6 - Addrs Secure Area Network : [OK]
# Add ------------------
echo " |";
# Allow Forwarding SLAN (fec0::/10) <> ULA (fc00::/7)
# network range : fc00:0000:0000:0000:0000:0000:0000:0000-fdff:ffff:ffff:ffff:ffff:ffff:ffff:ffff
echo " + IPv6 - Forwarding Addrs SWAN 2 ULA Networks -------------------------";
echo " |\\\\";
$IP6TABLE -A FORWARD -s fec0::/10 -d fc00::/7 -j ACCEPT
$IP6TABLE -A FORWARD -d fec0::/10 -s fc00::/7 -j ACCEPT
echo " | +--> fec0::/10 <?> fc00::/7 : ACCEPT";
echo " | |";
echo " | "+ IPv6 - Forwarding Addrs SWAN 2 ULA Networks : [OK]
echo " |";
}
function nat_v6()
{
WAN_IF="bridge0"
CT_WEB="fc01::192:168:10:100/128"
# NET FOR LXC EXCEPT TO THE ULA (fc00::/7) NETWORK
$IP6TABLE -t nat -A POSTROUTING -o $WAN_IF -s $CT_WEB ! -d fc00::/7 -j MASQUERADE
echo " "+ NAT : [OK]
}
Preferred lifetime
Je vous ajoute en plus, la préférence de Vie d'une adresse IPv6.
si un « container » (ou une machine du réseau local) a une adresse IPv6 ULA (avec passerelle ULA) et une GUA, on peut fixer la préférence de vie sur la GUA à 0 seconde, comme si elle était obsolète. Cà permet de pouvoir rentrer sur la GUA (malgré tou) mais de pourvoir attraper le(s) local(s) en utilisant l’adresse ULA (je n’ai pas trouvé comment-faire dans windows).
-
preferred_lft forever→preferred_lft 0sec– deprecated (obsolète)
$ ip -6 address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 state UNKNOWN qlen 1000
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0@if5: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 state UP qlen 1000
inet6 2a01:cb1d:12:1c00:1ab3:126:42:dc0/112 scope global deprecated
valid_lft forever preferred_lft 0sec
inet6 fc01::10:126:42:dc0/112 scope global
valid_lft forever preferred_lft forever
inet6 fe80::216:3eff:fef3:56b/64 scope link
valid_lft forever preferred_lft forever
$ ip -6 address add 2a01:cb1d:12:1c00:1ab3:126:42:dc0/112 dev eth0
$ ip -6 address change 2a01:cb1d:12:1c00:1ab3:126:42:dc0/112 dev eth0 prefer 0
Neighbor proxy
Je vous ajoute cela aussi, les adresses voisines proxy-fiante de l'IPv6 GUA.
Quand on a un bloc GUA IPv6::/64 (par exemple) et plusieurs sous-réseaux, pour qu’on puisse accèder à une adresse GUA (d’un sous réseau) il faut ajouter l’adresse IPv6 comme étant une adresse voisine proxifiante.
Par exemple notre serveur principal à 2 cartes ethernet – eth0 et eth1 – sur eth0 (2a01:cb1d:12:1c00::1) on a LA connectivité Internet et sur eth1 on distribue un autre réseau pour des machines locales. Sur eth1 on a une machine, disons la GUA 2a01:cb1d:12:1c00:beef:0000:0000:0001.
Déjà vérifier que la configuration IPv6 est correcte :
Sur la carte eth0 (-r lire et -w écrire):
sysctl -r net.ipv6.conf.eth0.forwarding = 1
sysctl -r net.ipv6.conf.eth0.accept_ra = 2
sysctl -r net.ipv6.conf.eth0.proxy_ndp = 1
Sur la carte eth1 :
sysctl -r net.ipv6.conf.eth1.forwarding = 1
sysctl -r net.ipv6.conf.eth1.accept_ra = 2
sysctl -r net.ipv6.conf.eth1.proxy_ndp = 1
Donc, sur le routeur il faut déclarer une machine comme voisine à la carte ayant la connectivité Internet pour qu’on puisse y accèder de l’exterieur (internet).
root@routeur:~ # ip -6 neighbor show proxy
2a01:cb1d:12:1c00:beef::1 dev eth0 proxy
Exemple :
root@routeur:~ # ip -6 neighbor delete proxy 2a01:cb1d:12:1c00:beef::1 dev eth0
root@routeur:~ # ip -6 neighbor show proxy
Test depuis l’extérieur :
root@machine_externe:~ # ssh -6 2a01:cb1d:12:1c00:beef::1
ssh: connect to host 2a01:cb1d:12:1c00:beef::1 port 22: No route to host
root@routeur:~ # ip -6 neighbor add proxy 2a01:cb1d:12:1c00:beef::1 dev eth0
root@machine_externe:~ # ssh -6 2a01:cb1d:12:1c00:beef::1
root@2a01:cb1d:12:1c00:beef::1’s password: OKKK
Ciao. Bonne journée à tous !
Romain.





%20A+.png)
.png)










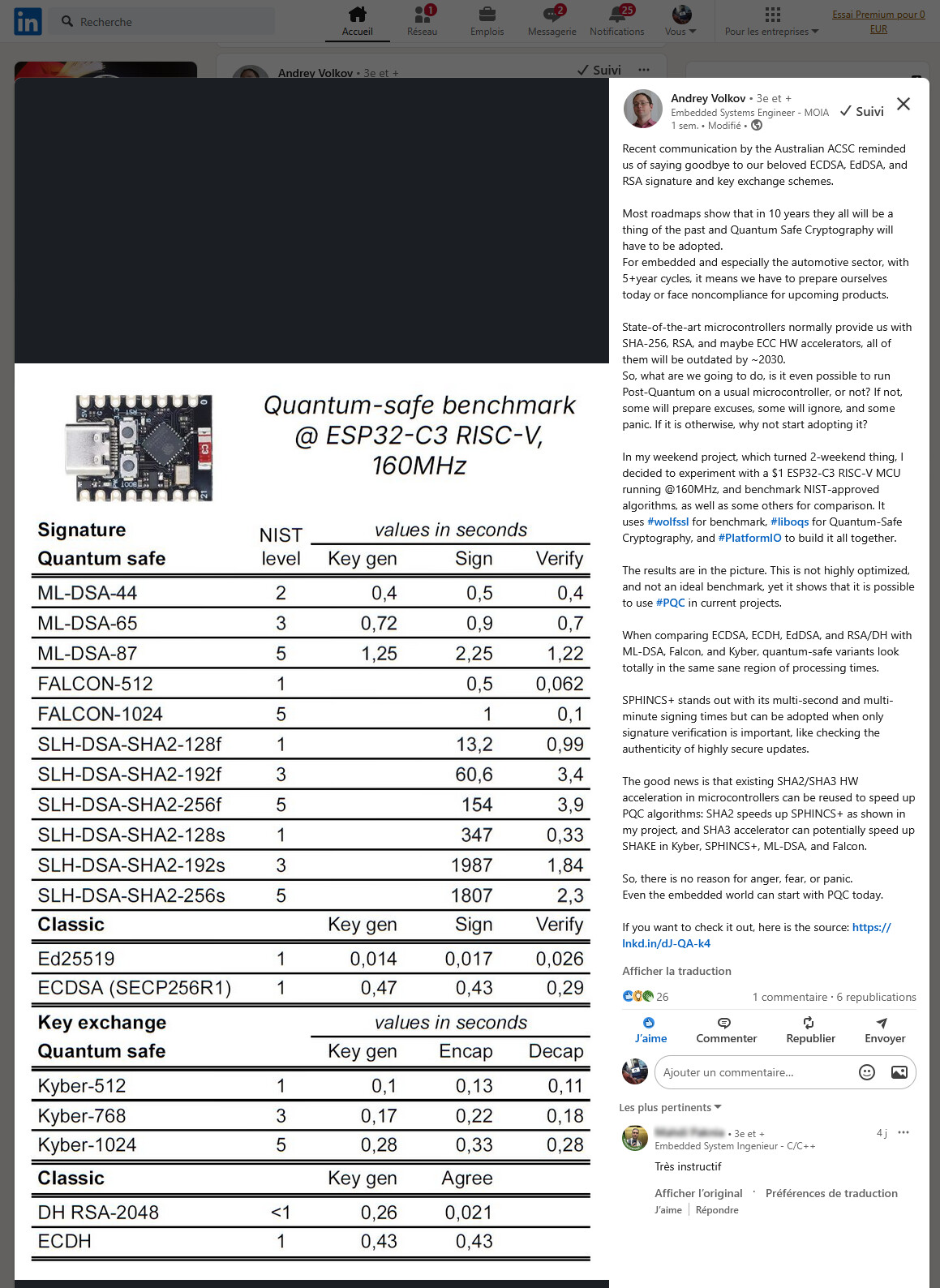




 j’ai ouvert ce sujet sur FaceBook, tu me crois
j’ai ouvert ce sujet sur FaceBook, tu me crois 


 France !
France ! Langue
Langue 
 How to configure strongSwan v6 Post-Quantum Cryptography NIST compliant #2731
How to configure strongSwan v6 Post-Quantum Cryptography NIST compliant #2731